)
Threat actors are using a new zero-day vulnerability to target the HTTP/2 protocol for Rapid Reset DDoS attacks. The vulnerability is tracked as CVE-2023-44487 and can be used to exploit HTTP/2’s stream cancellation feature by repeatedly sending and immediately canceling requests. Cybersixgill observed threat actors on popular cybercrime forums spreading two different proofs-of-concept for Rapid Reset DDoS.
THE HEADLINE
Cloudflare[1] recently announced the discovery of a novel form of Distributed-Denial-of-Service[2] (DDoS) attacks called HTTP/2 Rapid Reset. As the name implies, this vector targets the HTTP/2[3] protocol to disrupt networks with debilitating floods of traffic. The key to this vector is a zero-day vulnerability tracked as CVE-2023-44487,[4] which attackers abuse HTTP/2’s stream cancellation feature by repeatedly sending and immediately canceling requests. Threat actors automate the request-cancel process, which knocks servers and applications offline.
Researchers noted that Rapid Reset attacks require a relatively small-sized botnet[5] (~20,000 machines), a fraction of the size of other botnets observed by Cloudflare, which can reach millions of machines. This means Rapid Request attacks produce far greater numbers of requests, with fewer resources.
Threat actors launch DDoS attacks for a number of reasons, ranging from political motivations to revenge and economic sabotage. In some cases, attackers use DDoS tactics to extort money from victims, demanding payment to cease attacks. DDoS attacks can also be used as a smokescreen during other malicious activities, such as data theft. Regardless of the motivation, DDoS attacks can disrupt business operations and cause financial and reputational harm.
According to reports from Cloudflare, Google, and Amazon AWS, HTTP/2 Rapid Reset attacks have outpaced the scale of previous DDoS attack vectors by three times. Indeed, HTTP/2 Rapid Reset attacks have reached over 200 million requests per second (RPS), which is far greater than both the average apex of around 50-70 RPS and the previous record of 71 million RPS. To illustrate the scale at which attacks are growing, prior to the 71 million RPS attack, the previous record was 46 million RPS in June 2022.[6]
According to Cloudflare, DDoS attacks are becoming more frequent and powerful. Indeed, the amount of HTTP DDoS attacks documented by Cloudflare surged by 79% year-over-year in 2022, and the number of volumetric attacks exceeding 100 billion bits per second[7] (Gbps) increased by 67% quarter-over-quarter (QoQ). In addition, Cloudflare also observed an 87% QoQ increase in the number of attacks lasting over three hours during 2022.
In response to the uptick in DDoS attacks, the FBI launched an international law enforcement effort called Operation PowerOFF[8] to combat criminal activity threatening Internet infrastructure and legitimate users’ access to it. As part of the effort, the FBI partnered with the UK’s National Crime Agency and the Police of the Netherlands to display search engine ads deterring people looking for DDoS services.[9]
DIVING DEEPER
The Cybersixgill Investigative Portal detected interest in CVE-2023-44487 on popular cybercrime forums, in addition to proofs-of-concept (PoCs) for HTTP/2 Rapid Rese circulating on a clear web site. The activity observed by Cybersixgill includes the following October 13, 2023 post on a popular English-language cybercrime forum in which a threat actor posted a PoC for CVE-2023-44487, referring to it as HTTP/2 Rapid Reset. The poster is an active forum member, but appears to be relatively inexperienced, which is evidenced by their other posts seeking access to ransomware-as-a-service (Raas) operations and questions[10] about DDoS attacks related to the current Israel-Hamas conflict.
While this PoC appears to have been posted by a security researcher, threat actors frequently abuse such exploits, even if they are posted for “educational purposes.” Furthermore, the circulation of PoCs on forums such as this one also significantly increases the risk of attacks leveraging vulnerability.
 Figure 1: A forums member posts a PoC for the HTTP/2 Rapid Reset flaw
Figure 1: A forums member posts a PoC for the HTTP/2 Rapid Reset flaw
Cybersixgill also collected the October 10, 2023 post below from a member of a Russian-language cybercrime forum, seeking a PoC for CVE-2023-44487. In response, another forum member provided a link to a PoC. This is a separate PoC from the one in the post above, illustrating the spread of exploits designed to leverage the HTTP/2 Rapid Reset attack vector.
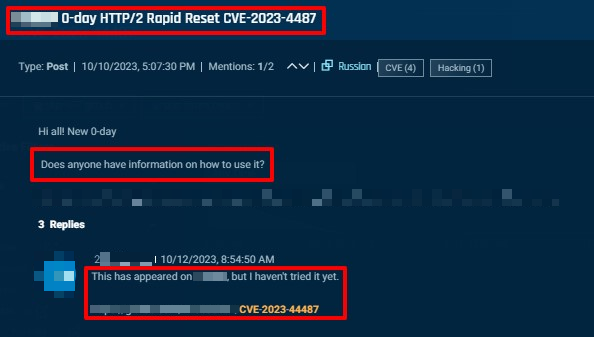 Figure 2: A forum member posts another PoC for the HTTP/2 Rapid Reset flaw
Figure 2: A forum member posts another PoC for the HTTP/2 Rapid Reset flaw
TAKEAWAYS
HTTP/2 Rapid Reset DDoS attacks are breaking records, causing alarms to sound about this new threat. As the most severe HTTP DDoS attack-type reported, interest in CVE-2023-44487 is likely to increase among threat actors. While the reasons for such attacks range from political agendas to financial motives, such attacks can often be carried out by relatively unsophisticated actors.
Due to the potential effects of large-scale DDoS attacks on both direct victims and related entities, all organizations should implement proper security measures to reduce the attack surface and the impact of possible DDoS campaigns. Among these measures, organizations should address all known vulnerabilities, avoid exposing corporate resources to ports, protocols or applications from which connection is not required; place critical resources behind Content Delivery Networks (CDNs) or Load Balancers; and limit Internet traffic to specific sections of the corporate infrastrucure.
[1] Founded in 2010, Cloudflare, Inc. is an American content delivery network and DDoS mitigation company.
[2] A volumetric DDoS attack floods a network with a massive amount of data, overwhelming its resources and available bandwidth. These attacks are difficult to defend against as they often originate from a wide range of sources, utilizing botnets to generate high volumes of traffic.
[3] Hypertext Transfer Protocol (HTTP) is an application-layer protocol for transmitting hypermedia documents, such as HTML. It was designed for communication between web browsers and web servers, but can also be used for other purposes.
[4] Cybersixgill’s CVEs Scoring Mechanisms assigned CVE-2023-44487 its highest score (5.75) on October 12, 2023, with the Common Vulnerability Scoring System (CVSS) reaching 7.5 by October 15, 2023.
[5] A botnet is a network of computers infected by malware and under the control of a single attacking party, known as the “bot-herder.” The owners of botnet-infected computers are generally unaware of the malware.
[6] That was an increase of roughly 80% more than the previous record in June 2022, involving an HTTPS DDoS of 26 million RPS that Cloudflare mitigated.
[7] Gbps stands for billions-of-bits-per-second and is a measure of bandwidth on digital data transmission mediums such as optical fiber.
[8] Operation PowerOFF is a joint operation between the FBI, the United Kingdom's National Crime Agency, Dutch police, and Europol, which displays warning ads in search engines when people search for booter services. These ads lead to a Cyber Choices page that offers information about the use of cyber skills and advice to use them in a legal manner. A similar advertisement from the FBI points users to a website operated by its Anchorage office, which explains why DDoS attacks are illegal and the consequences of engaging in such activity.
[9] For example, a search for “booter service” on Google produces a message stating, "Looking for DDoS tools? Booting is illegal."
[10] Ransomware-as-a-Service (RaaS) is a business model for licensing ransomware variants in the same way that legitimate software developers sell SaaS products. RaaS provides even those with very little technical knowledge the ability to perform ransomware attacks by signing up for a service.
)
)
)
)